Note: This guide is not very stable, use at your own risk, do not go into this without some understanding of *nix, and the ability to solve problems and google and stuff. Also snort was not designed for wireless, this configuration will not work with wireless at all. There are hacky patches you could maybe apply to get snort to work with kismet or something (I didn't look too far into it) but honestly at that point it would much easier to choose a more light weight IDS
This is a post Jordan and myself had been talking about writing since the last meeting. Snort is a wonderful open source Intrusion Detection System (IDS) which is very effective as a first response system when your machine is being attacked, or as a line of defense in computer security related games like Capture the Flag (CTF)
I decided to set it up on my local machine for fun (since it's not very necessary on a machine not running services, but fun to have) as well as give me the ability to step through the process. I'm setting up the Snort IDS utilizing the postgres SQL database (because I already have it setup for metasploit interaction).
Installation
1. I'm running on a 64 bit Ubuntu 11.10 install (though it should be similar for all *nix platforms
2. You will need to uncomment every line that starts with deb in /etc/apt/sources.list (remove the leading (#)
3. after uncommenting those lines run the command: sudo apt-get update to have access to the new repositories.
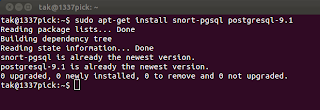 4. execute the command ~$ sudo apt-get install snort-pgsql postgresql-8.4 (you see 9.1 in the picture, ignore that I've found 8.4 is easier to deal with for this setup.
4. execute the command ~$ sudo apt-get install snort-pgsql postgresql-8.4 (you see 9.1 in the picture, ignore that I've found 8.4 is easier to deal with for this setup.5. you will be greeted with a window that tells you to execute some commands post-install, tab to the ok button then hit enter - I will post these commands next.
6. after the installation execute these commands
~$ su postgres
$ createdb snort
$ zcat /usr/share/doc/snort-pgsql/create_postgresql.gz | psql snort
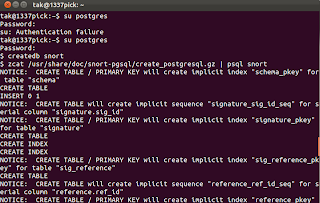 7. You should see a bunch of text, this is a good sign, you've just setup your sql database for snort, now we have to create a user snort can access.
7. You should see a bunch of text, this is a good sign, you've just setup your sql database for snort, now we have to create a user snort can access.8. execute the command
$ createuser -P snort
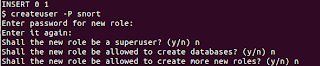
9. create a strong password for snort, then answer no to all of the questions it will ask you
10. Login to your new database with the command
$ psql snort
11. Now grant snort permissions to do anything to it's database by running:
snort=# grant all privileges on database snort to snort;
and now the database is all setup! :)
Pop open the database config file with
~$ sudo nano /etc/snort/database.conf
Remove the line where you see output database: log, postgresql and replace it with:
output database: alert, postgresql, user=snort password=your-snort-password dbname=snort host=localhost
12. Now we need to edit some configuration files in postgres
~$ sudo nano /etc/postgresql/8.4/main/postgresql.conf
Hit ctrl+w and type listen_addresses then enter now uncomment that line so it is
listen_addresses = 'localhost' Hit ctrl+x then hit enter to save those changes
13. We are going to open up postgres to snort sensor connections now
~$ sudo nano /etc/postgres/8.4/main/pg_hba.conf
A few lines down you should see a line like
#host DATABASE USER CIDR-ADDRESS METHOD [OPTIONS]
uncomment this and change it to:
host snort snort 127.0.0.1/32 password
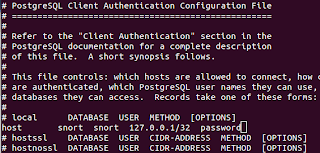
Hit Ctrl+x and enter to save those changes
14. Now restart postgres to apply those changes ~$ sudo /etc/init.d/postgresql restart
15. Lets setup some permissions for the snort configuration file now
~$ sudo chown root:snort /etc/snort/snort.conf
~$ sudo chmod 755 /etc/snort/snort.conf
~$ sudo chown root:snort /etc/snort/database.conf
~$ sudo chmod 755 /etc/snort/database.conf
16. Now we need to configure some debian based specific options
~$ sudo nano /etc/snort/snort.debian.conf
Fill in DEBIAN_SNORT_HOME_NET="Your network ip/subnet bits (ex. 192.168.1.0/24)"
DEBIAN_SNORT_INTERFACE="Your network interface (ex. eth0)"
Ctrl+x -> enter to save
17. test snort with a command like
~$ snort -i eth0 -c /etc/snort/snort.conf
If this did not work, it's probably an issue with your HOME_NET variable in snort.debian.conf
I wrote a Subnetting calculator last year with CIDR support that may help located here platform independent, launches through webstart. There is also an android version I released on the android market, if you search for "Open Subnet Calculator"
18. Next run this command
~$ sudo apt-get install apache2 libapache2-mod-php5 php5-gd php5-pgsql libphp-adodb
After that's finished, open the apache php.ini file
~$ sudo nano /etc/php5/apache2/php.ini
Ctrl+w search for "extension=", and add under the comments the following (if they are not already present in the file):
extension=pgsql.so extension=gd.so
19. Restart apache to load the new modules
~$ sudo /etc/init.d/apache2 restart
20. Install acidbase
~$ sudo apt-get install acidbase
When asked select the postgres database, and enter a password for acidbase
21. When that is finished execute this command
~$ sudo nano /etc/apache2/sites-available/default
Hit Ctrl+W search for Hit the up arrow key so the cursor is right above it
Hit Ctrl+R and in the file to insert field enter /etc/acidbase/apache.conf
Scroll up to allow from 127.0.0.0/255.0.0.0
Change that to your local network/subnet mask. - once again the subnetting calculator I linked to earlier may help if you are confused.
Hit Ctrl+X and then Enter to save.
22. You should now be able to access acidbase through the URL http://127.0.0.1/acidbase/, except replace 127.0.0.1 with your local ip address,
Click a link that says "Setup" Then click a link that says "Create BASE AG" down on the left side click the Main Page link, which will display snort statistics.
I hope I helped a person or two :)
References:
A lot of information was gained through these tutorials
http://www.howtoforge.com/intrusion_detection_snort_base_postgresql_ubuntu6.06 <- outdated but a lot of good info, I primarily used this but updated stuff for the changes in the software
http://en.gentoo-wiki.com/wiki/Snort#Setup_Snort_with_PostgreSQL <- this tutorial helped me figure out some of the changes I needed to make to the steps involved with the older software.
http://www.aboutdebian.com/snort.htm - Helped with a lot of the acidbase stuff
when is configured whit postgres where is the logs?, or how can i see the alerts? plz and thanks
ReplyDeleteI read your post on CIDR calculator. Your post is very important to the students for understanding the concept of CIDR calculator.
ReplyDelete